Common Scams
Your security is a priority at TDECU. We will never ask for your online or mobile banking username or password via phone or text.

Phishing and vishing: What are they?
Phishing is a fraudulent attempt to obtain sensitive information, such as your username, password, and credit card details, through email and instant messaging.
Vishing is when scammers use fake phone numbers or email addresses to pose as trusted people or organizations, such as a TDECU employee or security officer, to gain access to your bank details, credit card numbers, and other personal information.
How to protect yourself from phishing scams:
-
Use security software
Install security software on your computer and set it to automatically update.
-
Protect your smartphone
Set your smartphone to automatically update to the latest software version.
-
Use multi-factor authentication
Two authentication methods makes it more difficult for fraudsters to access your private information.
-
Back up your data
Keep your personal data safe, such as on a secondary hard drive.
-
Know our security policy
TDECU will NEVER ask for your personal information, such as your Social Security number.
How to protect yourself from vishing scams:
-
Be suspicious of unknown callers
Do not give callers your personal information. Hang up and block the numbers.
-
Do not trust caller ID
Be aware of caller ID spoofing. Make sure you know all callers before answering.
-
Ask callers questions
Ask suspicious callers who they are, who they work for, and their phone number.
-
Do not press buttons or respond to prompts
If you get an automated message, hang up and block the number.
-
Register with the National Do Not Call Registry
Adding your phone numbers to the National Do Not Call Registry can help reduce, but not eliminate, spam callers.

Secret shopper scams: What are they?
Secret shopper scams can appear as legitimate job postings for mystery shoppers at retail stores. However, these fraudulent shopper programs will often ask you to wire money using Western Union or MoneyGram. If a secret shopper opportunity is legitimate, you will never be asked to pay an application fee, deposit a check, or transfer funds to someone else.

Malvertising: What is it?
Malvertising is the use of online advertising to spread malware. Typically, it involves injecting malicious ads into legitimate websites. Fraudsters host these ads on reputable websites, which gives them access to unprotected web users who are not keeping their personal information safe behind a firewall.

Social engineering: What is it?
Social engineering is a scam that involves manipulating people into sharing their personal information, like passwords, bank information, computer access, and more. Typically, the scammers pose as trusted sources through emails, instant messages, or texts. Common scams include installing antivirus software and refinancing homes.
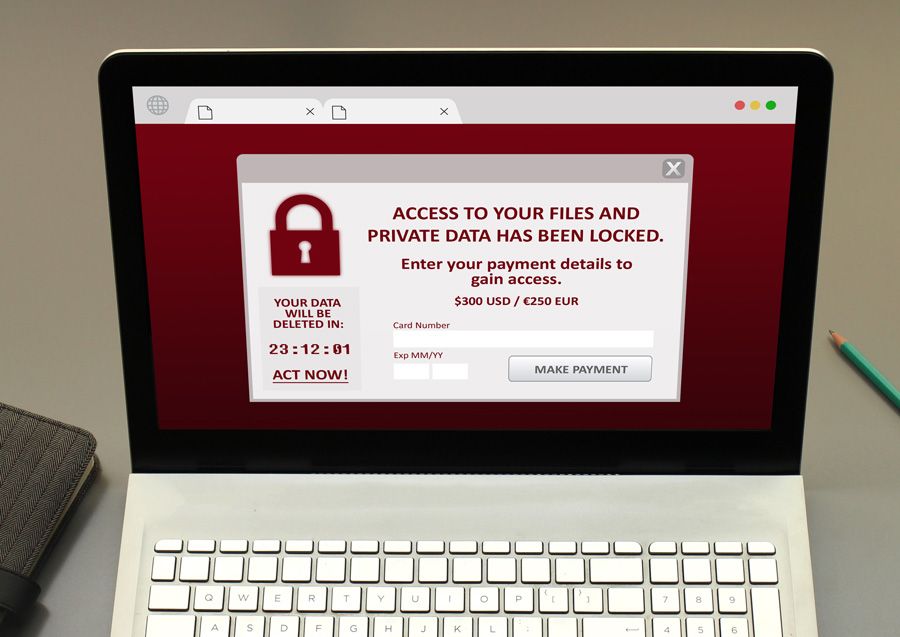
Malware and ransomware: What are they?
Malware is malicious software that can harm a computer or smartphone. It may include computer viruses, worms, trojan horses, or spyware. Ransomware is a form of malware that works by invading a computer and encrypting files. The attacker then demands a ransom from its victim to restore access to the files.
Contact TDECU about any suspicious activity
If you have been contacted by anyone saying they are from TDECU and requesting your personal information, or you feel uncomfortable about your personal information in any way, contact us immediately. We will help you protect your accounts.